How Cyber Deception Helps CISOs Meet Their Cybersecurity Goals
12 September 2022 | by Xavier Bellekens

CISOs are under constant pressure to secure their organizations’ data and systems from ever-evolving cyber threats. As the number and sophistication of attacks continue to grow, traditional security measures such as firewalls and antivirus software and even EDR are no longer enough. This is where cyber deception comes in.
The use of cyber deception to strengthen cybersecurity defenses is relatively new. Cyber deception involves fooling attackers into thinking they have succeeded in breaching a network, when in reality they have only accessed a monitored environment, allowing CISOs to identify and deflect the attackers. By doing so, CISOs can buy themselves valuable time to detect and respond to the attack. In addition, cyber deception can provide valuable intelligence about adversaries’ tactics, techniques, and procedures. This information can be used to improve the organization’s overall security posture. As the benefits of cyber deception become more widely known, CISOs are increasingly turning to this proactive security measure to help protect their organizations from harm.
CISOs’ Challenges
One of the biggest challenges faced by CISOs is managing the increasing complexity of IT security. CISOs need to have a deep understanding of a wide range of technologies in order to secure enterprise networks and technology stacks.
This comes with challenges such as:
- The inability to detect a breach in the network early
- Understand the attack surface
- Detect insider threats in a timely manner
In addition, CISOs need to be able to effectively communicate with both technical and non-technical stakeholders about the risks posed by new technologies and the steps that need to be taken to mitigate those risks.
This comes with challenges such as:
- Obtain funding the for the SOC and CTI teams
- Increase the cybersecurity maturity of the organization
- Avoid technical challenges
With the COVID-19 pandemic and the uptake in remote work, CISOs have faced challenges is managing security in an increasingly remote world. With more employees working remotely, CISOs need to find ways to secure enterprise data and systems without restricting employee productivity.
This comes with challenges such as:
- Reduce false positives generated by the current technology stack in place
- Miss key alerts
- Meet regulatory demands for breach detection and investigation
Finally, CISOs need to have a good overview of the threats their organization is facing.
- Detect threats with valid credentials
- Detect APT and zero-day threats
These challenges, alone, make the job for CISO extremely complex, and these challenges are then deferred to their SOC team and threat intelligence teams. Impacting the entire organization.
To summarize
The main pain points of CISOs are
- The inability to detect a breach in the network early
- Understand the attack surface
- Detect insider threats in a timely manner
- Reduce false positives generated by the current technology stack in place
- Miss key alerts
- Meet regulatory demands for breach detection and investigation
- Detect threats with valid credentials
- Detect APT and zero-day threats
- Increase of alert fatigue
- Difficulties to reduce SOC personnel turn over
Each of these pain points can increase the risk of a successful data breach, costing the organization millions of dollars in damages. It is key for the leadership team to define a cohesive strategy to manage risk appropriately and proactively.
How Can Cyber Deception Help CISOs?
As the use of cyber deception technologies continues to grow, it is important for CISOs to become familiar with the different cyber deception products. While all vendors offer some basic features, there are significant differences in terms of functionality, price, and deployment model. As a result, it is important to choose a vendor that best meets the needs of your organization. One vendor may offer a better price, but another may offer more features. It is also important to consider the deployment model, as some vendors offer on-premise solutions while others offer cloud-based solutions. By taking the time to learn about the different vendors and their products, CISOs can ensure that they choose the right solution for their organization.

Lupovis Snare is designed to deploy deception assets inside and outside your network. Leading to a strengthened security posture, advanced threat intelligence, and high-fidelity alerts before being breached.
Deceptive Assets
The deception platform must have a wide range of deceptive assets and provide excellent telemetry. This telemetry is essential for obtaining contextual information on the attacker. Without this information, it can be difficult to accurately identify the source of an attack. Additionally, the platform must be able to rapidly deploy new assets in response to changes in attacker tactics. This agility is essential for keeping ahead of the attacker and protecting the network. By carefully designing the deception platform and selecting the right assets, it is possible to obtain the information needed to identify attackers and protect networks.
Events and Alerts
In the world of security, false positives are a major issue. A false positive is when an event is incorrectly flagged as suspicious when it is actually benign. This can cause a lot of wasted time and resources as SOC teams frantically try to track down a non-existent threat.
Analysts also often suffer from “alert fatigue” due to the high volume of false positives generated by security tools that are triggered unnecessarily, wasting the analysts’ time and energy. In some cases, false positives can even lead to burnout. The Lupovis Snare platform is designed to produce zero false positives; therefore, the event alerting concise, clear and feature-rich. By eliminating false positives, SOC teams can be confident that they are only looking at real threats, which will save a lot of time and effort in the long run.
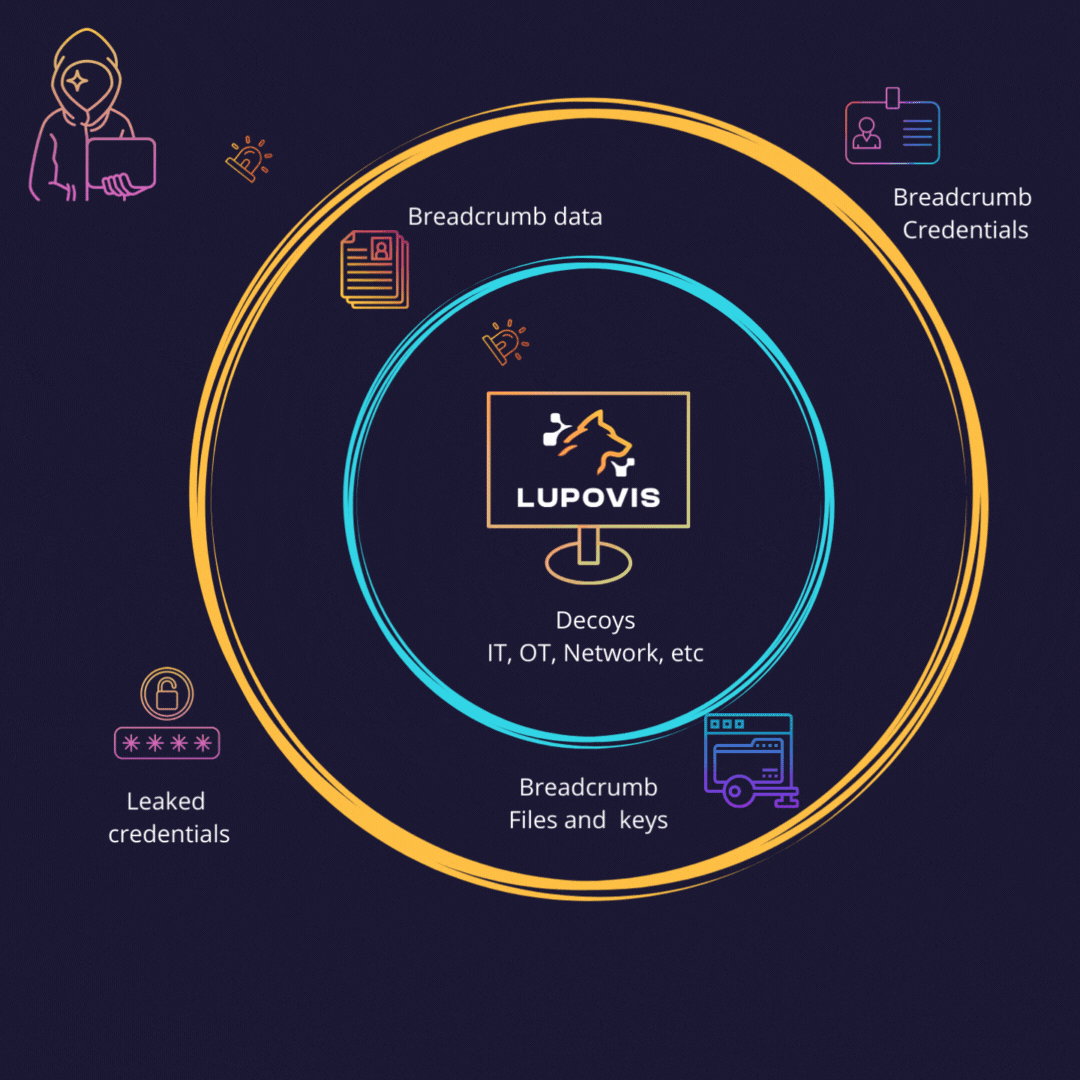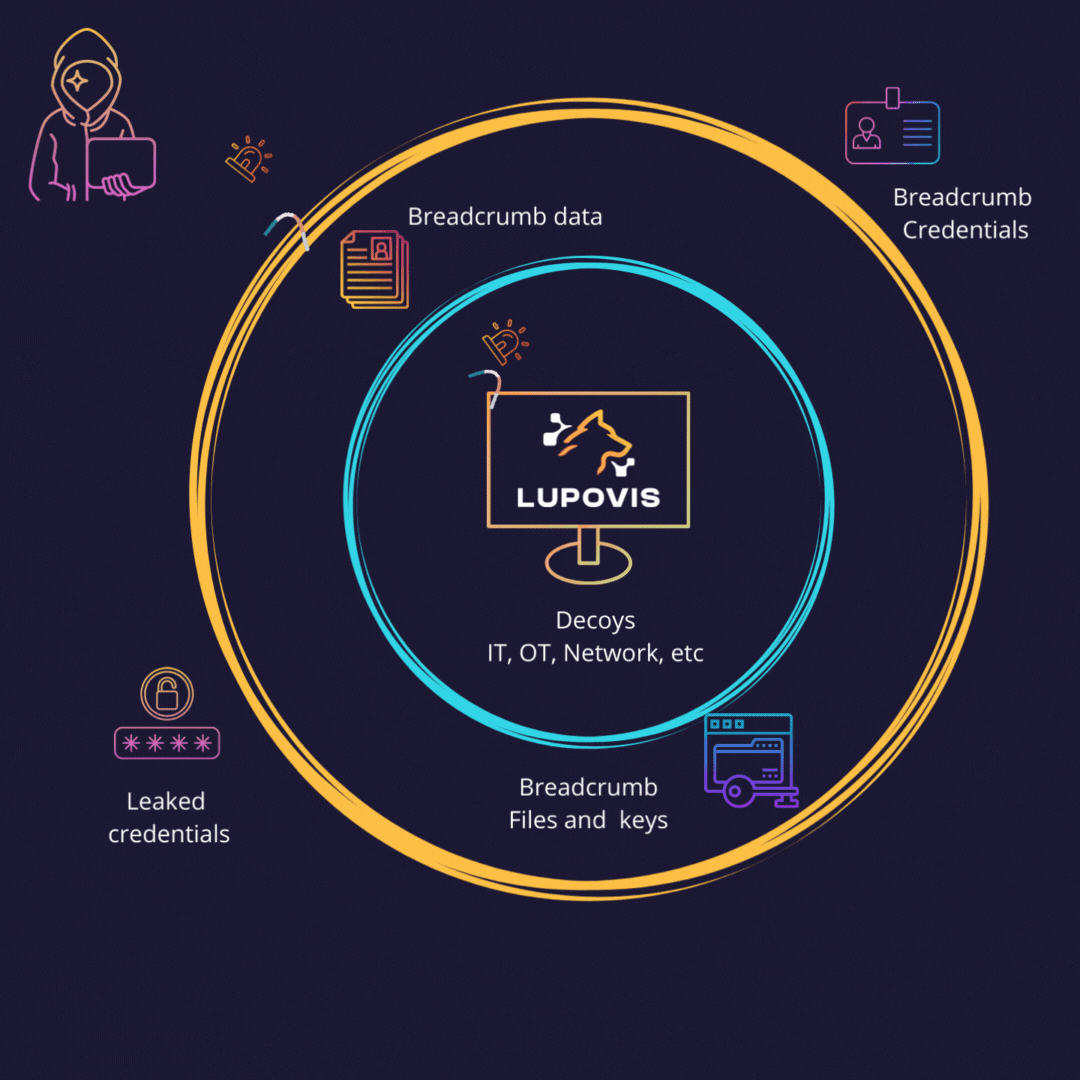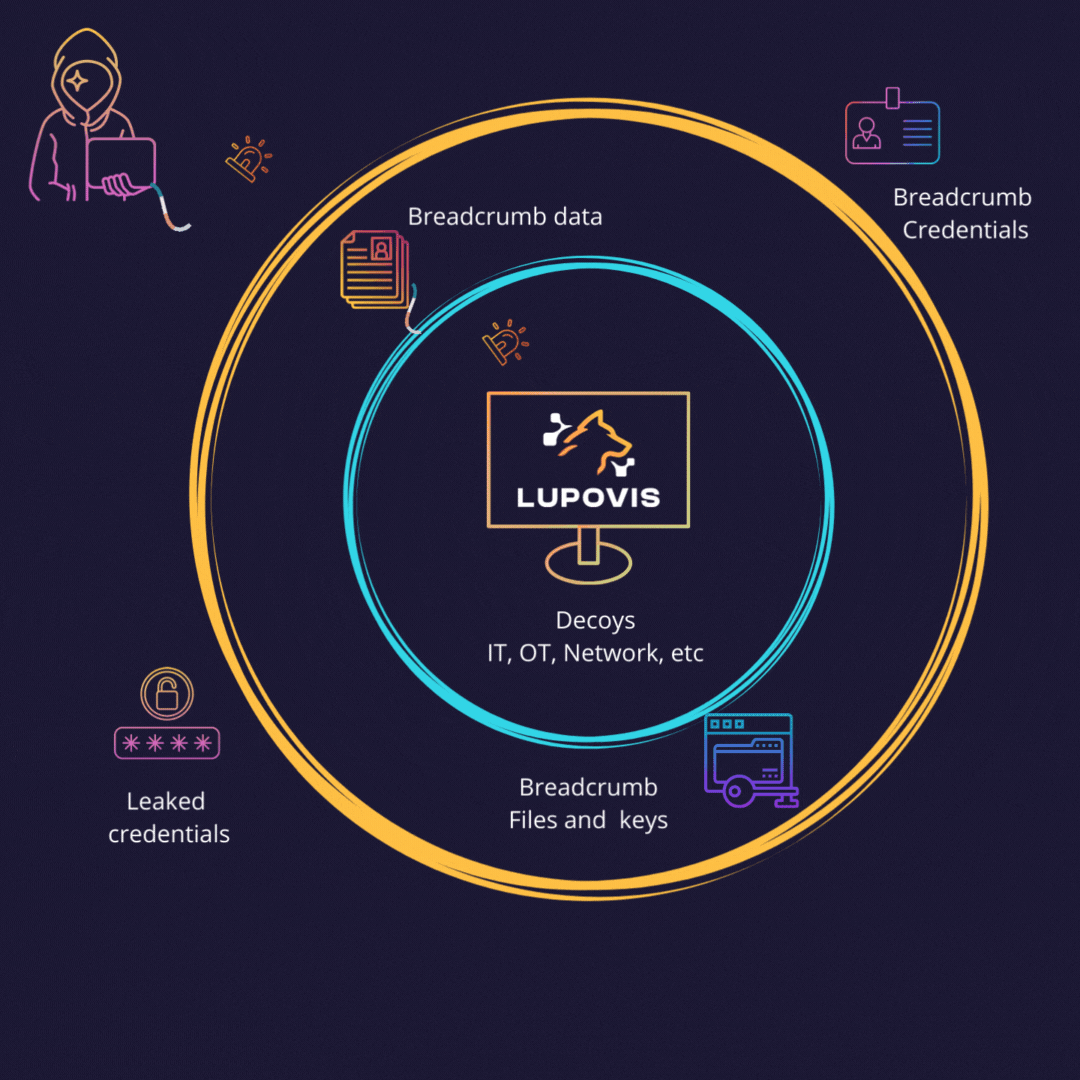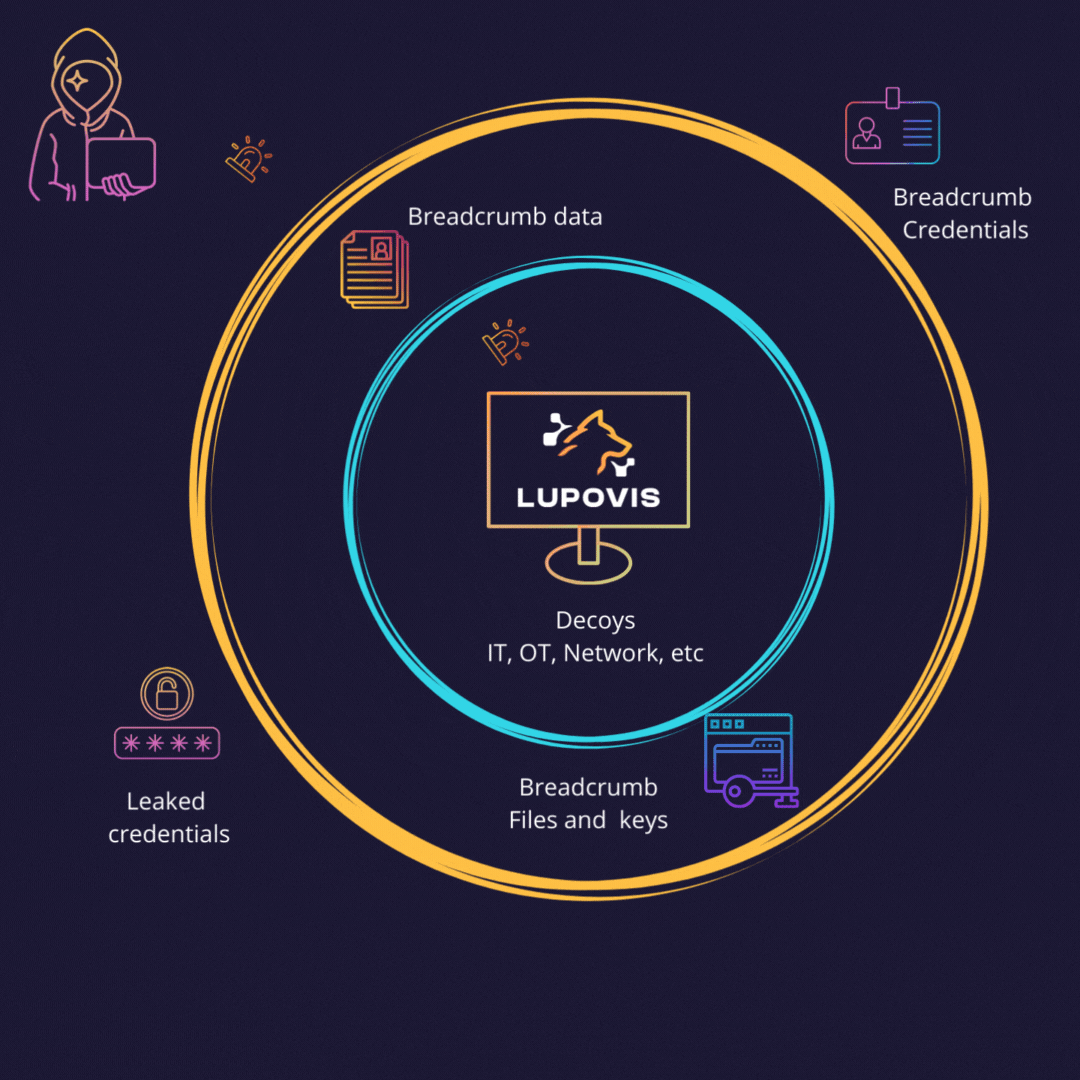
Leading on with Breadcrumbs and Lures
A cyber deception breadcrumb is a small piece of information left behind for an attacker to use and trigger an alert. Deception breadcrumbs can be placed by security teams inside and outside the network in order to bait attackers to reveal themselves. By following the breadcrumbs, attackers unwittingly expose themselves and their methods, leading to high alert fidelity.
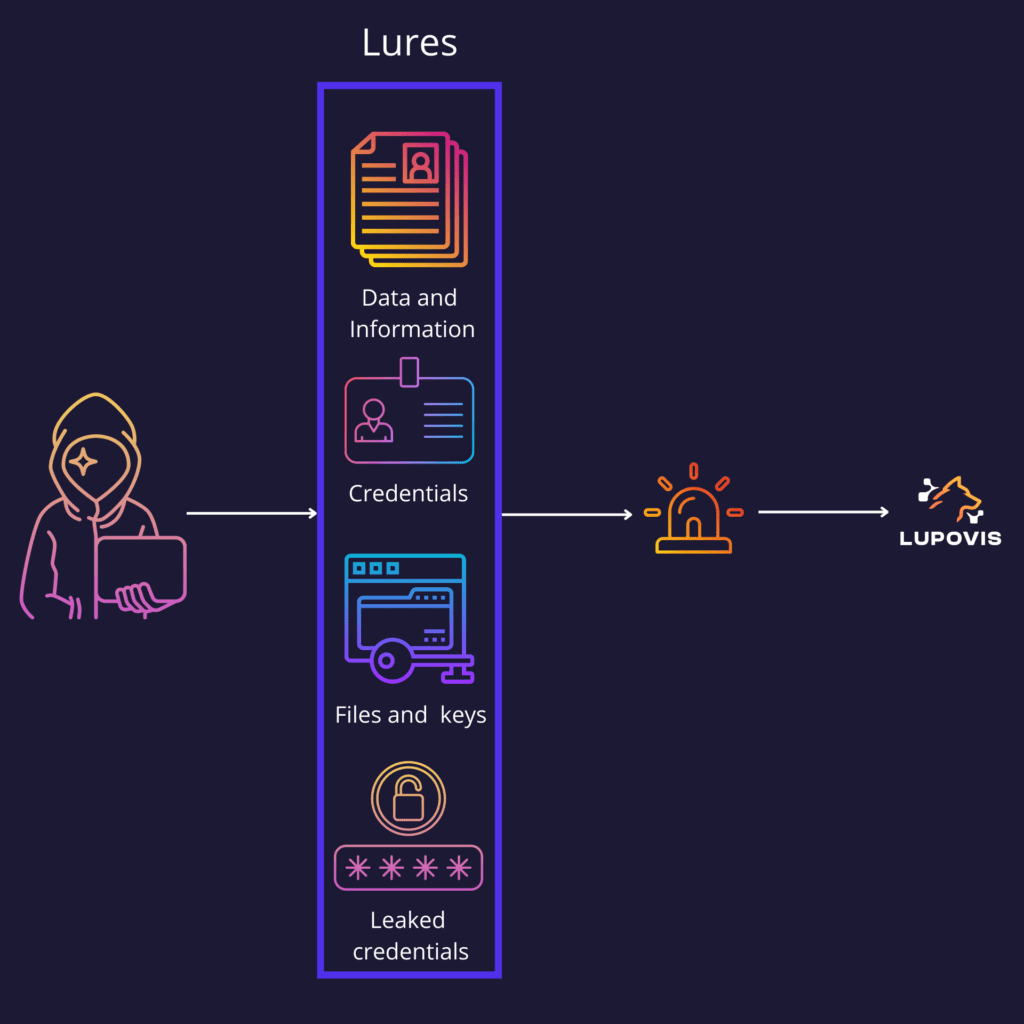
By using breadcrumbs, organizations can detect adversaries early and take action to mitigate the threat. Breadcrumbs can also be used to track activity and uncover patterns. They can be left behind by SOC teams and can be used to detect changes in behavior or unusual activity. By monitoring breadcrumbs, organizations can detect malicious activity early.
Breadcrumbs also have the potential to distract and mislead attackers, making it more difficult for them to succeed.
Conclusion
Cyber Deception is a powerful tool for CISOs looking to solve a variety of regulatory challenges, increase visibility in their network, and reduce the number of false positives their SOC team is facing.
When an attacker takes the bait, they are revealed and can be stopped before causing any damage. Deception has become an increasingly popular solution for CISOs as it offers a number of advantages and is an incredibly effective way to comply with a variety of regulations, such as GDPR and HIPAA.
Deception also allows to
- Enhance the detection of insider threats
- Detect faster and at lower costs
- Collect contextual intelligence on the threats they face
- Reduce false positives and only obtain high fidelity alerts
- Obtain the ability to communicate effectively with management on the true number of threats seen, as opposed to list opportunistic threats
- Potential to reduce the security spend
Ultimately, deception platforms can help to reduce the probability of a data breach, regardless of the source. For CISOs, this is a vital consideration, as any data breach can have serious consequences for an organization. As such, the use of a deception platform should be considered as part of any comprehensive data security strategy.
12 September 2022 | by Xavier Bellekens
Speak to an Expert
Whether you have a specific security issue or are looking for more information on our Deception as a Service platform, simply request a call back with one of our security experts, at a time that suits you.