How Does Cyber Deception Work and Why Should you Care?
2 March 2022 | by Xavier Bellekens
Cyber deception is a technique used to consistently trick an adversary during a cyber-attack. It works by deceiving adversaries with fabricated services and fictitious documents. Fabricated services are called Honeypots. They deliberately imitate services such as SSH, FTP, RDP, to create uncertainty and confusion in the adversary’s mind. The aim is to influence the adversary as early as possible and turn the tables in favour of the defender.
If that sounds complicated, it’s because it is. But if you want to increase your cybersecurity posture, you need a basic understanding of how cyber deception work. That’s what you’ll learn in this guide.

Before we get into the technical stuff, let’s first make sure we understand what cyber deception actually is, why it exists, and why any of this even matters.
What is cyber deception?
Cyber deception is a technique used to consistently trick an adversary during a cyber-attack.
Cyber deception consists of two main parts
- Psychology. The state of mind of the adversary during the engagement.
- Technology. The services, documents, honeypots used to trick the attacker.
What is the aim of cyber deception?
Every deception solution aim to provide defenders with the upper hand, before, during and after a cyber-attack. That’s how they obtain or maintain market share—at least in theory.
Other objectives include
- Providing threat intelligence. How the attackers behave (ahead of a cyber-attack)
- Decreasing dwell time. Detect the attacker early (during a cyber-attack)
- Produce forensic metrics. The tactics, techniques, and procedures used (during and after a cyber-attack)
Why should you care how deception work?
Understanding how cyber deception can trick attackers, will help you defend better ahead of cyber-attack.
If you can turn the tables ahead of an attacker, you, as defender, do not need to be right 100% of the time. On the other hand, adversaries now must dodge every honeypot, decoy and faux services you created, in order to stay silent. Improbable and almost impossible.
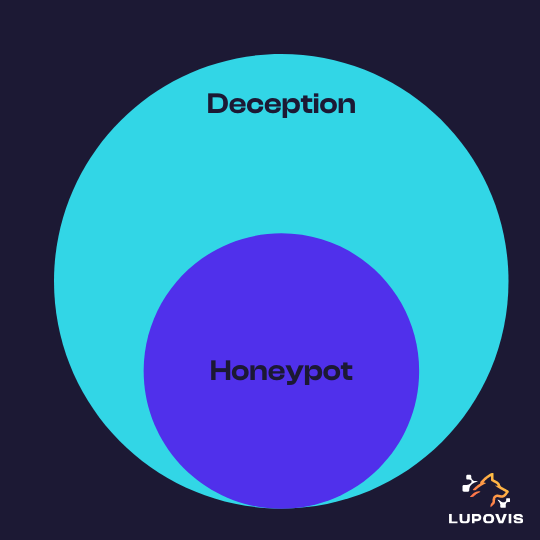
What is the difference between cyber deception and honeypots?
Honeypots and cyber deception are very much related, but they’re not quite the same thing.
Early honeypots were designed to attract adversaries at the network edge. Cyber deception on the other hand is the holistic approach of deceiving an attacker consistently ahead and during a cyber-attack. This can be done using manipulation techniques, lies, false information. Furthermore, deception can be used both at the network edge and within the network to detect lateral movement.
The MITRE corporation released the MITRE Engage framework, adding to its more well-known MITRE ATT&CK® matrix. The framework puts cyber deception technology at the centre of its strategies for active defence. The National Institute of Standards and Technology (NIST) has also recently releases guidance that emphasized the role of deception technology for cybersecurity.
How does Cyber Deception Work in Practice ?
Certainly not “in mysterious ways”, so, let’s drill deeper into the mechanisms used to place and maintain a deceptive environment.
Step 1 : Cyber Deception Placement
Cyber-security teams should scatter deceptive assets across their infrastructure.
- Decoy services. Users should place services such as SSH, FTP, RDP and others in subnets that contains similar services. For example, placing a PLC decoy in a subnet that doesn’t contain any operational technology is counterproductive.
- Decoy files. The security team can place decoy files and breadcrumbs on user computers to lead a potential attacker towards a specific decoy. Note that this strategy also increases the risk of false positives.
- Decoy objects. When en voyage, the CEO may want to leave a decoy laptop and cell phone in his ro, to detect an evil maid attack.
When analysing the attack surface of the organization, the security team should increase the number of decoys close to the potential entry points. For example, they may want to increase the number of decoys in the same IP range as the inbound VPN. More decoys should also be placed closer to the crown jewels of the organization (i.e.; an EDR, a PLC, a production line, or the accounting subnet).
Step 2: What is Cyber Deception Coverage ?
Cyber deception coverage is the ratio between real assets and deceptive assets in the network.
When an adversary penetrates a network via phishing, or through an exploit, they have to move laterally. Therefore, if the network contains only 100 real assets, the adversary has 99 other options. When covering 10% of the network with decoys, the adversary has 1 in 10 chances of hitting one when moving laterally.
Most deception solution will advertise for a higher coverage, ranging from 20% to 100% of the network, tremendously increasing the power of deception. However, increasing the amount of deceptive assets will also increase the number of resources needed for deployment and maintenance.
In Reality
Your deception coverage should be decided based on your needs, the architecture of the organization and coupled with a good strategy. The being said, in some cases a low coverage can also be beneficial, let us explain;
The path of an adversary when penetrating a network isn’t linear, despite what vendors would like you to think. In fact, the path looks more like an inverted tree.
At each step of the exploitation, the adversary will have to make choices, which in turn will inform their path from the entry point to the finish line. You can influence each of the choices made by the attacker.
Subtle cues, such as low-hanging fruits, vulnerable services and key documents names, can tremendously increase the ability of the defender into tricking an attacker to reveal themselves. For example, attackers can be drawn to a file called “User Logins.xls” on a computer or to a misconfigured file server. Insider threats will also behave very differently than a script kiddie for example.
What constitute an acceptable coverage?
You can attain an acceptable coverage when the various path an attacker can take in the network hit at least one decoy, whether a honeypot, a honeyfile, a breadcrumb or any other type of deceptive asset.
Step 3: Alerts
The main advantage of cyber deception is, undeniably, alert fidelity. As only the IT security team, managed service provider or threat intelligence team is aware of the deception assets deployed within the environment, every alert is critical.
Let us explain;
When you deploy breadcrumbs, honeyfiles or honeypots and other deceptive assets within the organization to create your deception environment, your team, and you are the only ones, aware of the existence of these decoys. Hence, anyone, or anything interacting with the trap, will raise an alert.
This alert should then be investigated with a high priority.
Step 4: Threat Intelligence
Once an adversary starts interacting with the deceptive assets, data are being collected.
This allows your team to gain insight into the tactics, techniques and procedures used by the attacker. The intelligence captured can then be used by your blue team to
- Stop the attackers in their tracks as soon as an alert is raised
- Reinforce security measures
- Use the data for training
The red team on the other hand can use the data for
- Training
- Improve and / or simulate their next engagement
- Study to better protect the organization
Honeypots deployed at the border of the network can also help identify zero-days and collect data on new types of attacks such as log4j.
How to Deceive Attackers?
Strategy
The strategy is simple, place decoys that are similar to your environment. For example, do not deploy a Programmable Logic Controller (PLC) on a subnet that doesn’t contain any PLCs. Use the same naming convention, and use decoys that may tempt the attacker.
Customization
All your decoys must be attuned to your environment. To increase effectiveness, tune the decoys and use your own branding.
Breadcrumbs
Breadcrumbs are pieces of information you can use to lure attackers towards decoys. They can be any type of information that an attacker may use subsequently.
You should however be aware that, breadcrumbs may also lead genuine users towards your decoys, hence increasing your false positive rate.
References
- Intrusion Detection Honeypots: Detection through Deception by Chris Sanders
- Cyber Deception: Overview and the Road Ahead
- Lying to attackers: An Overview of Cyber-Deception and the Road Ahead
2 March 2022 | by Xavier Bellekens
Speak to an Expert
Whether you have a specific security issue or are looking for more information on our Deception as a Service platform, simply request a call back with one of our security experts, at a time that suits you.


