Understand the attacker perspective
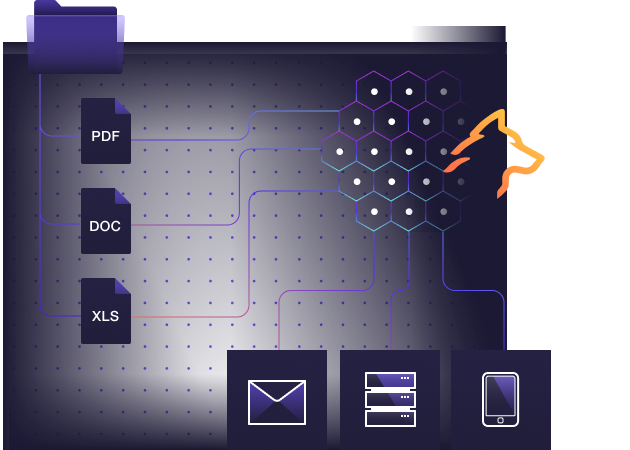
Detecting insider threats is extremely difficult. Organizations however, can turn the table on attackers by leveraging cyber deception and breadcrumbs technology to provide insider threats with faux information whether they are a contractor, an employee, a supplier or any other trusted party having access to your organization.
Using Lupovis, security teams can quickly identify unauthorized document access and download, credential theft or re-use, or simply an attempt to access and steal data. By creating deception assets, documents, files, credentials, and network shares and many other elements planted within your environment, Lupovis can quickly detect and alert a policy violation.
10/10 on Vision and Detection
The Lupovis platofm identifies insider threats in a matters of minutes and with no friction
High Fidelity Detection
Insight into misconfiguration and exposed data
Detect data theft attempts
Speak to an Expert
Whether you have a specific security issue or are looking for more information on our Deception as a Service platform, simply request a call back with one of our security experts, at a time that suits you.