Honeynet vs Honeypots
12 July 2022 | by Xavier Bellekens

How is a honeypot different from a honeynet?
A honeypot is a single service or computer on a network, that is configured to act as a decoy, attracting and trapping would-be attackers. A honeynet on the other hand is a network of honeypots that are used to lure in attackers and study their activities across multiple honeypots. Both honeynets and honeypots can be used to detect attacks, and collect data.
What is a honeynet?
Honeynets are a great way to study the behaviour of hackers. They’re designed with two or more honeypots, which look and behave like real systems or network services so that would-be intruders will be attracted for you to capture them on film!
🍯 To learn more about honeypots, have a look at our recent article What is a Honeypot in Cybersecurity?
How does a honeynet work?
Honeynet network work by luring in potential attackers with the promise of valuable data or access to a system. Once the attacker is on the honeynet, one or more honeypots can be used to observe and collect data about the attack. This data can then be used to improve the security of real systems and prevent future attacks.
The purpose of this network is to gather intelligence on the attacker and diverts them from your real network with fake information or “honey” as well as wasting their time.
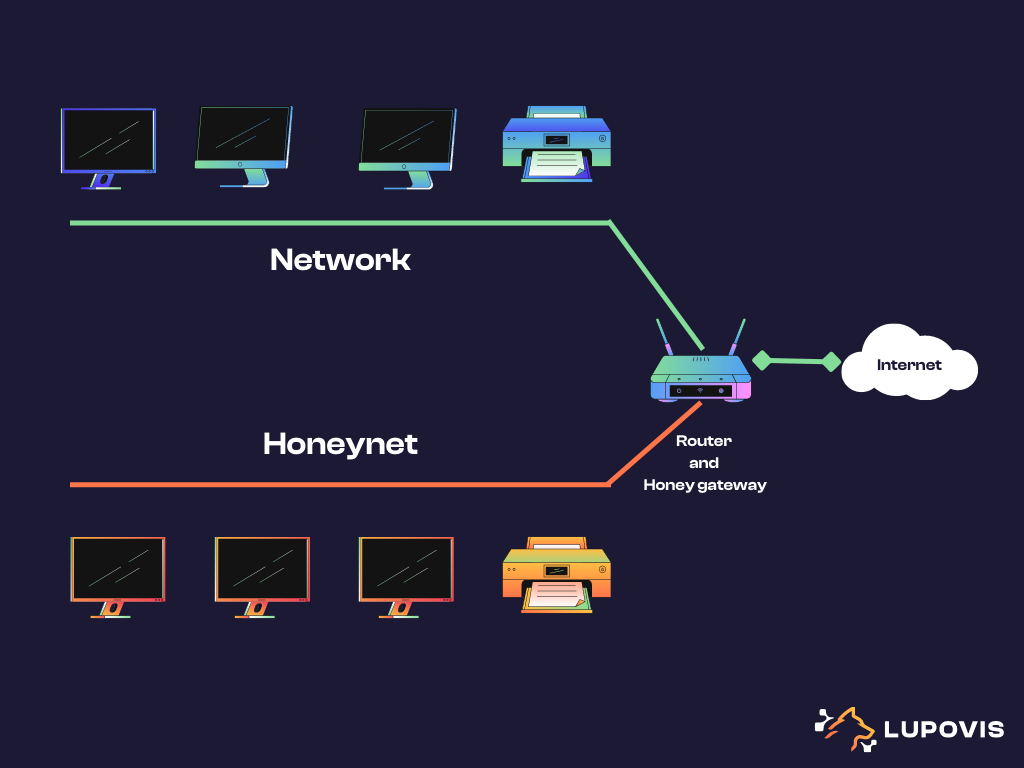
By creating a dedicated network segment, the legitimate systems and production network are isolated from the decoy network. This set up allows for low interaction honeypots and high interaction honeypots to be deployed for tracking hackers across multiple systems or Linux honeypot machine such as t-pot.
Recreating a “decoy” production network allows for threat intelligence team and security experts, to collect data on the network activity of adversaries by providing them with an attractive target. The honeynet may contain known vulnerabilities, various flavoured operating system, information systems, servers and much more. Having multiple honeypot instances, allows for the attacker to progress through the network segment and leave more breadcrumbs behind, such as Tactics, Techniques and Procedures (TTPs), Indicator of Compromise (IoC) and Indicator of Attacks (IoA).
The data captured, can help improve network security, the computer systems and mitigate risk and better protect the organization.
Honeynets provide additional protection than just building walls around your network with a firewall and intrusion detection system, etc, as each of the honeypots will gather and collect network traffic, IP addresses, zero-day exploits, and more information that can be used to improve your network security.
Why making your own honeypot or honeynet might be a bad idea?
Honeypots and honeynets can provide valuable security information, hence the temptation to create one from scratch might be great, however, there are a number of risks associated with creating your own. First, honeypots and honeynets can attract more attacks than would otherwise occur, putting your systems at greater risk. You would have to keep track of all the libraries used as well as do code reviews to ensure that none can be exploited further. Secondly, if not properly configured, honeypots and honeynets can themselves be exploited, providing attackers with a back door into your network. Finally, creating a honeypot or a honeynet, setting them up and maintaining them can be time-consuming and expensive.
That being said, you can use our curated list of free and open source honeypots to start with. Open source honeypots also have a lower risk of security vulnerabilities because anyone can audit the code for potential issues. And if a security vulnerability is found, it can be fixed quickly by the community of developers working on the project.
What is the difference between honeypot and cyber deception
In the cybersecurity industry, the terms “honeypot” and “cyber deception” are often used interchangeably. However, there is a key difference between the two concepts. A honeypot is a system that is deliberately designed to lure in potential attackers. By contrast, cyber deception is a technique that uses false information, systems and services to mislead or trap an attacker. In both cases, the goal is to bait attackers into revealing their true intentions or to gain information about their methods. However, deception is considered an active defence, that makes use of a range of techniques including honeypot to fool cyber adversaries into revealing themselves, their capabilities, and their intentions both in production network and decoy networks.
Honeypots and honeynets on the other hand are generally considered to be more passive and used for studying adversaries. Deception techniques are also tailored to the networks they are deployed in. Having deception decoys set up inside and outside the network provide an accurate picture of what intentions attackers or an insider threat may hold towards you; whether it’s forgathering intelligence or understanding the spread of malicious activity. As a result, cyber deception can be a more effective way of identifying and stopping attacks.

What are the benefits of using a honeynet ?
There are many benefits of using honeypots, including:
- The ability to detect attacks that might otherwise go unnoticed
- The ability to collect data about attacks and attackers, improving your indicator of attacks (IoA) and indicator of compromise (IoC)
- The ability to study the behaviour of attackers
- The ability to distract and mislead attackers
What is the difference between IDS and honeypot?
A honeypot is a computer system that is set up to bait users or systems into attacking it, in order to gain information about the attack and/or the attacker. A honeynet is a network of honeypots – usually a larger, more complex system. An IDS (intrusion detection system) is a security system that monitors network traffic and looks for suspicious activity that could indicate an attempted break-in. While honeypots and IDS systems both have their own strengths and weaknesses, they are not the same thing. One key difference is that honeypots and honeynets are designed to be attacked, while IDS systems are designed to detect attacks through network monitoring. This means that honeypots can provide more detailed information about an attack, but they also carry a greater risk of being breached
Conclusion
Honeypots and honeynets are both tools that can be used to detect attacks, collect attack data, and study the behaviour of attackers. However, there are some key differences between them. Honeypots are single computers that are configured to look and behave like real systems, while honeynets are networks of honeypots.
For learning about adversaries without the hassle of setting up, and maintaining honeypots, try Lupovis Snare, our dedicated cyber deception platform now.
12 July 2022 | by Xavier Bellekens
Speak to an Expert
Whether you have a specific security issue or are looking for more information on our Deception as a Service platform, simply request a call back with one of our security experts, at a time that suits you.