Implementing a FortiGate External IP Block List with Lupovis Prowl Dynamic
30 October 2023 | by Xavier Bellekens

Introduction
Welcome, network security professionals and enthusiasts,
Dynamic IP blocklists have emerged as a pivotal tool in safeguarding networks against real-time threats. Today, we delve into the integration of these blocklists with FortiGate’s sophisticated firewall capabilities.
FortiGate stands at the forefront, offering robust and flexible solutions tailored for modern security demands. By incorporating dynamic IP blocklists and utilizing an external block list (threat feed) in firewall policies for web filtering and DNS, we elevate our defensive strategies, ensuring an adaptive and proactive security posture.
In this guide, we’ll explore the practical steps and insights required for seamless integration, empowering you to enhance your network’s resilience against threats. Whether you’re fine-tuning an existing setup or embarking on a new security initiative, our goal is to equip you with knowledge and confidence.
Understanding Dynamic Blocklists
1.1 Introduction to Dynamic Blocklists
Dynamic blocklists, also known as threat feeds or real-time blocklists, are continuously updated lists of IP addresses, URLs, or domains associated with malicious activities. Unlike static blocklists, which require manual updates, dynamic blocklists can import and utilize an external IP list, providing a real-time response to emerging threats. They play a critical role in fortifying network defenses by preemptively blocking communications with known harmful entities.
1.2 How Dynamic Blocklists Function
Dynamic blocklists operate by pulling data from various threat intelligence sources, aggregating and analyzing it to identify malicious actors. These sources could include cybersecurity research organizations, threat intelligence sharing platforms, and other trusted entities that track and report on cyber threats.
Upon identification of a malicious IP address or domain, the dynamic blocklist is updated, and any attempt to communicate with these known threats is automatically blocked by the network’s firewall or security appliance. This process is ongoing, ensuring that the blocklist is always current and providing up-to-the-minute protection.
1.3 The Importance in Network Security
Implementing dynamic blocklists is paramount in today’s cybersecurity landscape for several reasons:
- Proactive Defense: They provide a proactive approach to security, allowing organizations to block threats before they reach the network.
- Resource Efficiency: Automating the threat blocking process saves valuable time and resources that would otherwise be spent on manual threat hunting and updating static blocklists.
- Adaptability: The dynamic nature of these blocklists means they adapt quickly to the ever-changing threat landscape, maintaining a high level of security.
- Firewall Policies: Dynamic blocklists can be integrated into firewall policies to block connections based on the listed IP addresses, enhancing overall network protection.
1.4 Examples of Threat Feeds and Blocklist Services
There are some threat feeds and IP blocklist services available, catering to different security needs and industries.
- Lupovis Prowl: A global threat intelligence feed providing data on known threats in real-time
For example, you can use an IP address threat feed in a local-in policy by creating lists of IP addresses and configuring firewall policies.
By integrating these services with FortiGate’s firewall, organizations can enhance their network security, ensuring a robust defense against malicious actors and potential cyber threats.
You can also integrate the blocklist and use our API with your WAF and SIEM to correlate malicious IPs as shown here under.
1.5 Obtaining the Lupovis Dynamic Blocklist
Lupovis provides unparalleled blocklists catering to a variety of specific security needs ranging from sectorial and geographical blocklists that are meticulously compiled to identify 0-day adversaries, human actors, bots, mass scanners, and a plethora of other potential threats to global blocklists.
This is made possible through an extensive network of sensors strategically placed across the internet, dedicated to analyzing and interpreting the incessant noise of online activity. These sensors work tirelessly, classifying and categorizing the internet’s cacophony in real-time, ensuring that Lupovis’ blocklists are consistently accurate, reliable, and up-to-date. Additionally, DNS filter profiles can be configured to block IP addresses in a threat feed list, enhancing the security measures.
As a result, organizations can trust in the efficacy of these blocklists to provide a robust layer of security, defending their networks against a wide array of cyber threats. With Lupovis, users are not just accessing blocklists; they are leveraging a comprehensive threat intelligence system that stands at the forefront of internet security.
To obtain our dynamic Blocklist use the Promotional code BLOCKLIST10 on our BASIC Plan, to get 10 percent off your first 6 months.
Configuring Dynamic Blocklists in FortiGate
Achieving a more secure network environment is pivotal, and integrating dynamic blocklists into your FortiGate firewall is a crucial step in this journey. This section provides a detailed guide on how to configure dynamic blocklists within the FortiGate environment.
2.1 Accessing the FortiGate Web Interface
- Open Your Browser: Launch your preferred web browser.
- Enter the FortiGate IP Address/Hostname: Type in the IP address or hostname of your FortiGate device into the address bar, followed by
:443to specify the port (e.g.,https://192.168.1.1:443). - Log in: Enter your username and password when prompted to access the FortiGate dashboard.
2.2 Setting Up Security Fabric
- Navigate to Security Fabric: In the left-hand menu, click on “Security Fabric”.
- Configure Security Fabric: Ensure that Security Fabric is enabled and properly configured to include all relevant devices in your network.
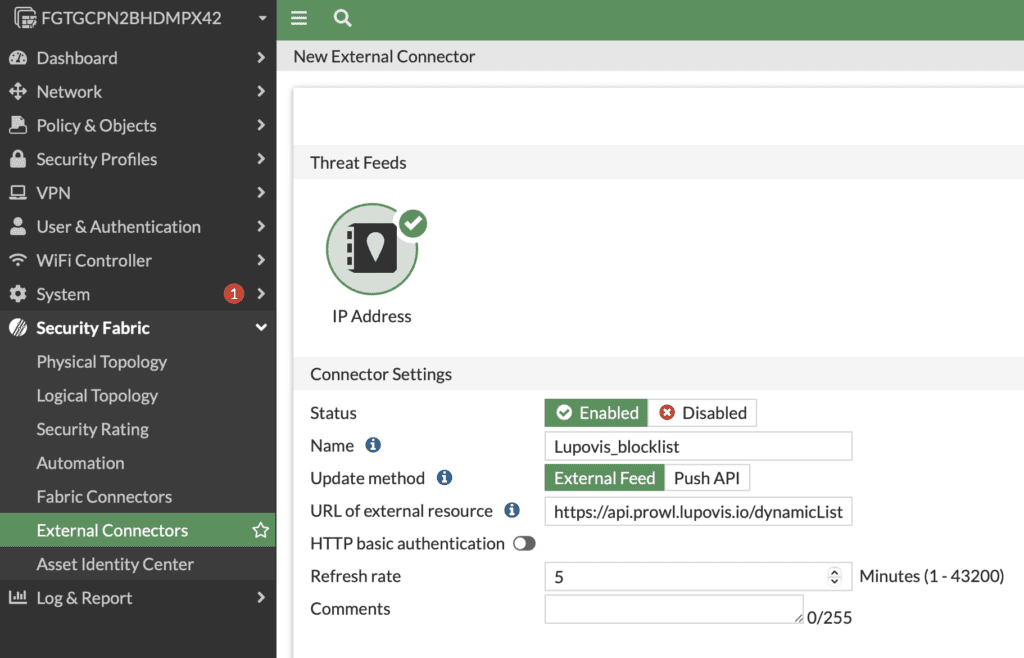
2.3 Configuring an External Connector
- Go to External Connectors: Within the “Security Fabric” settings, find and select “External Connectors”.
- Add a New Connector: Click “IP Addresses” or “Add” to setup a new external connector.
- Configure the Threat Feed:
- Name: Give the connector a descriptive name.
- Feed URL: Enter the URL of the dynamic blocklist/threat feed.
- Update Interval: Set how frequently FortiGate should pull updates from the threat feed.
- Test Connection: Ensure that FortiGate can successfully retrieve data from the threat feed URL.
2.4 Applying the Blocklist to Security Policies
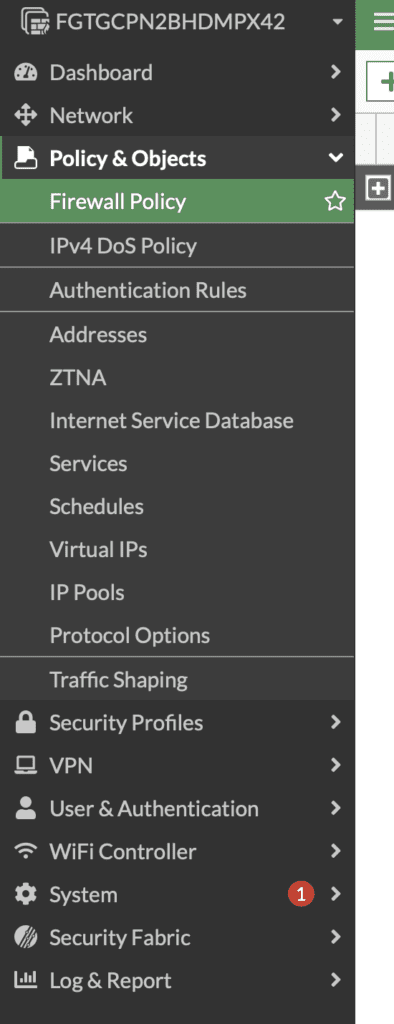
- Navigate to Firewall Policy: Under “Policy & Objects”, select “Firewall Policy”.
- Edit an Existing Policy or Create a New One: Choose a policy to edit or create a new policy where you want to apply the blocklist.
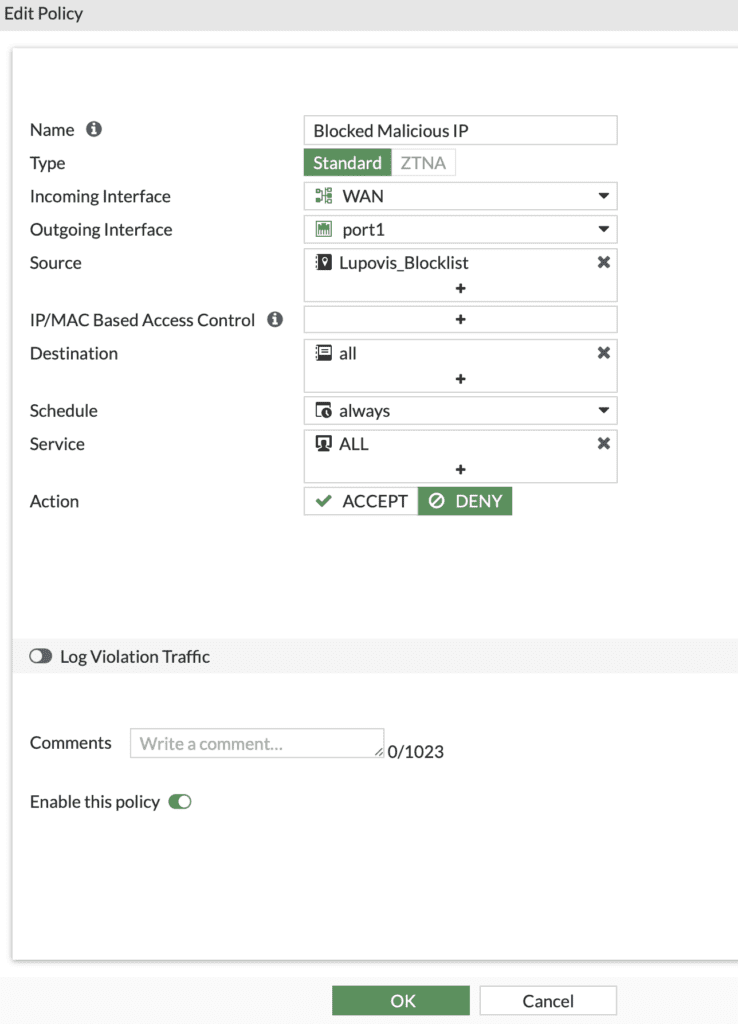
- Apply the External Connector:
- In the policy settings, locate the section for source or destination addresses.
- Add the external connector you’ve configured to the policy, in our case. Lupovis_Blocklist
- Configure the rules to match incoming traffic
- Right click and Edit CLI
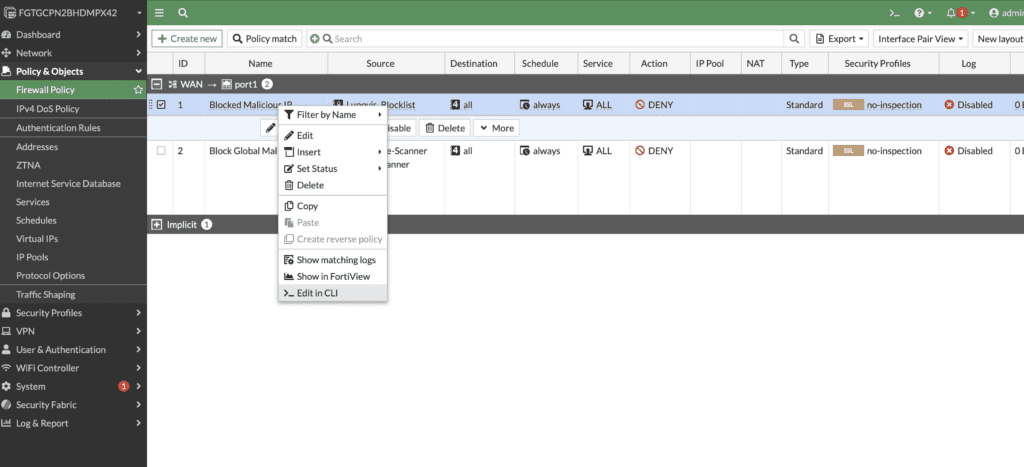
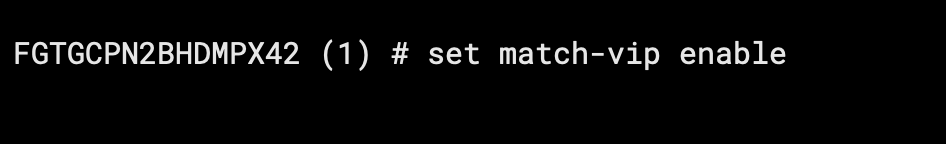
Type in Set match-vip enable
The set match-vip command in FortiGate’s firewall policy configuration is used to control how the firewall handles traffic in relation to Virtual IPs (VIPs) configured on the device.
When you configure a VIP on a FortiGate device, you are essentially setting up a rule to forward traffic from one IP address to another, usually from a public IP address to a private IP address behind the firewall. This is often used for services such as web hosting, where you need to make an internal resource available externally.
2.5 Verifying and Monitoring
- Monitor Traffic: Use the “Log & Report” section to monitor network traffic and ensure that the dynamic blocklist is actively being enforced.
- Regularly check that the IP are being updated
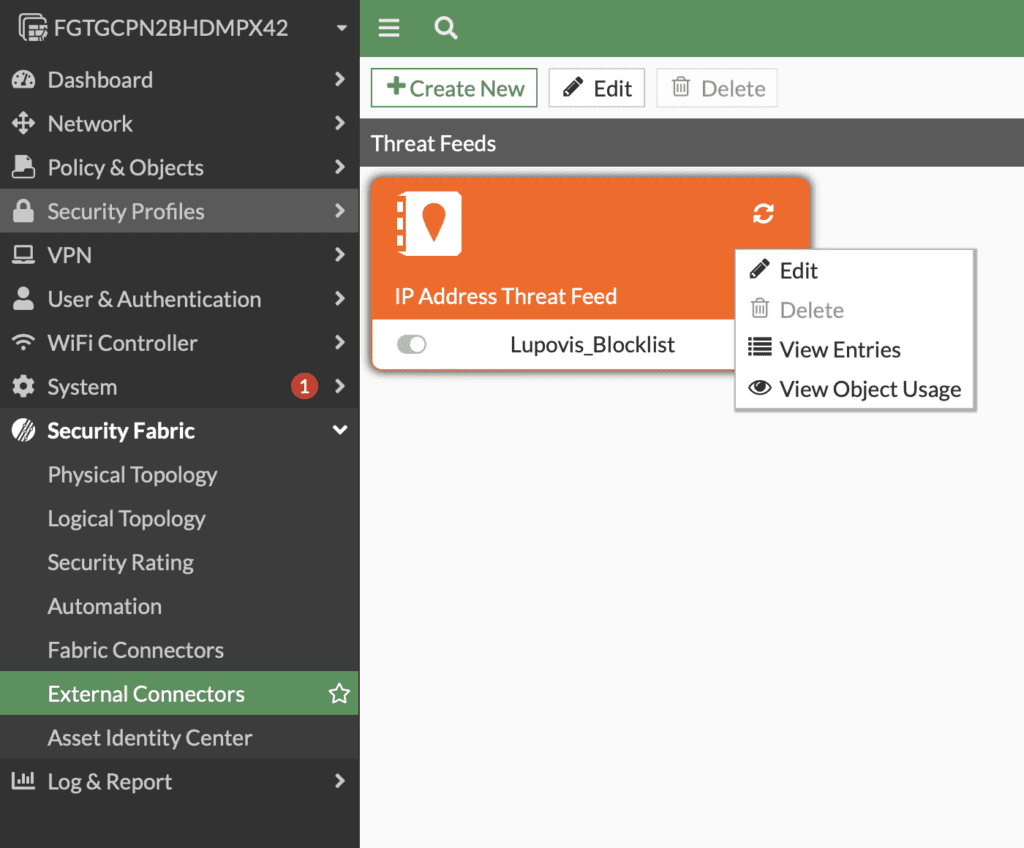
Conclusion
Congratulations on making it to the end of our comprehensive guide on integrating dynamic blocklists into your FortiGate firewall! By now, you should have a solid understanding of the critical role that dynamic blocklists play in maintaining a robust and resilient network security posture. Whether you’ve chosen to implement them directly or via FortiGate’s advanced Security Fabric and external connectors, the steps outlined above are designed to set you on the path toward enhanced cybersecurity.
Leverage Lupovis for Enhanced Protection: For those seeking access to highly reliable and specific dynamic blocklists, Lupovis stands ready to assist. Our specialized blocklists, both geographical and sectorial, are crafted to meet the diverse needs of organizations aiming to safeguard their digital assets. By choosing Lupovis, you are ensuring that your network benefits from the most up-to-date and relevant threat intelligence available.
Stay Proactive and Explore Further: We encourage all network security enthusiasts and professionals to stay proactive in their efforts to protect their networks. Beyond dynamic blocklists, FortiGate offers a plethora of features designed to enhance your security posture. Dive deeper, explore more, and remember – in the world of cybersecurity, vigilance is key.
Feel free to reach out to Lupovis for any queries integration of dynamic IP blocklists with FortiGate to enhance your network security. Discover step-by-step guides, best practices, and access specialized blocklists from Lupovis for tailored protection or assistance in accessing our dynamic blocklists, and take the next step in fortifying your network security today. Together, let’s create a safer digital space!
30 October 2023 | by Xavier Bellekens
Speak to an Expert
Whether you have a specific security issue or are looking for more information on our Deception as a Service platform, simply request a call back with one of our security experts, at a time that suits you.